Social Media as Evidence
 Over the last several years, social media has become an increasingly important tool in litigation. It also can be a hazard for attorneys who are not aware of their clients’ presence on the internet. Nowadays most people have at least one social media account. Content on the web may contain important information about parties and witnesses; not only is it a good idea to conduct a search for content online, arguably lawyers have an ethical obligation to do so.[1] What is reasonable depends on the circumstances, but at least some minimal effort should be made.
Over the last several years, social media has become an increasingly important tool in litigation. It also can be a hazard for attorneys who are not aware of their clients’ presence on the internet. Nowadays most people have at least one social media account. Content on the web may contain important information about parties and witnesses; not only is it a good idea to conduct a search for content online, arguably lawyers have an ethical obligation to do so.[1] What is reasonable depends on the circumstances, but at least some minimal effort should be made.
This article provides some suggestions for finding relevant social media content, and issues that need to be considered when dealing with such evidence at trial.
Searching for Content
I generally start with a Google search of parties and witnesses. It often captures individuals’ internet presence and my search can quickly focus on relevant social media platforms. I will also follow up with a search on Facebook, Instagram, and Twitter (there are obviously more sites to search, but often a Google search captures existing profiles across many platforms). If any profiles are public,[2] I scan them for relevant information, including looking for posts around the time of the subject incident.3] I also perform a Google search about the incident itself and see if there are any hits. If there is an article about what happened, I browse the comment section at the end of the article to see if anyone is worth investigating. If so, I perform the same search of that person as the one I do for parties and witnesses. This really shouldn’t take long, and, honestly, won’t yield anything in most instances. However, if you do find something, trust me – you will feel like a rock star.
Quick social media searches of potential jurors can be helpful too. You are likely to learn more about them than you will during voir dire.
Getting the Nuggets into Evidence
After you’ve discovered the nugget, getting it admitted at trial presents several hurdles. One obstacle is a hearsay objection to the underlying content. Since we are all hearsay experts, I’d like to focus on an issue often overlooked: authentication. Any judge is likely to question the genuineness of a social media post offered as evidence. In the age of the “deep fake”[4] laying the proper foundation for online evidence becomes more important.
While authentication is an issue, do not overthink it. Social media content may simply feel less reliable than other forms of evidence because anybody can post anything, but getting it admitted is relatively straightforward. When I first encountered social media content I wanted to use in a case, I freaked out. I figured I needed to obtain a copy by way of subpoena. How the heck do I subpoena a social media post? I hear companies like Facebook and Twitter object and fight subpoenas. Fortunately, a subpoena is not necessary for information accessible to the public.[5]
The rules for authentication are essentially the same in both California and federal courts. To authenticate any piece of evidence, including social media content, the key question is this: is the judge convinced that what is being offered “is what it is claimed to be.”[6] Is the document an actual Facebook post made by the defendant? Is the document an actual tweet the witness made?
One way to authenticate the evidence is to simply describe for the judge how you found it, including what steps you took. Explain why the profile where the post was made is likely that of the party or witness. Perhaps direct them to the website URL address so they can look it up themselves. Depending on your objectives or desired use of the content, this might suffice.
I often take another approach: I retain an investigator to retrace my steps and ask that they record in detail the steps taken and take screenshots of the relevant content. Best practice is to hire an investigator with an expertise in digital forensics that is highly experienced with social media investigations. When laying the foundation, you call the investigator during trial to testify that “it is what it is claimed to be.”
Above all else, the best way to authenticate a post, with the highest likelihood of getting it admitted, is having the author of the content testify they made it. If you take the deposition of the individual who made the post, confront them with it and get them to admit they made the post. In a recent deposition I confronted a defendant, who we were claiming was speeding and drove recklessly and caused the collision, with his Facebook post pictured below.
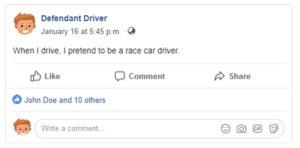
His response sounded an awful lot like “hummina hummina.”
Confronting Social Media Evidence Used Against Your Client
There are a few considerations when the other side is trying to use social media posts against your client. First line of defense is obviously attacking the foundation. How do we know “it is what it is claimed to be”? How do we know it is my client who made that post? Even if it appears that it was my client’s account, can the post truly be attributed to my client? What if others had access to my client’s iPad or computer and could have made the post?
One other thing to keep in mind is one of my favorite evidentiary rules, and one that I often use to get otherwise inadmissible hearsay of my client into evidence – the rules regarding completeness.[7] If the opposing party wants to cherry pick a post or two, offer into evidence other posts that contextualize the ‘damaging’ post, and paint your client in a better light. Perhaps choose the post about your client saving a baby from an alligator….
Relevant Caselaw
The most important California cases dealing with social media as evidence are People v. Beckley[8] and People v. Valdez.[9] Beckley did impose a requirement that expert testimony demonstrate that the images were not manipulated. However, People v. Goldsmith[10] clarified the requirements for admissibility of digital evidence does not include expert testimony. Further, Valdez held expert testimony was not required. In that case, sufficient foundation was laid when the page icon identifying the owner of the page displayed a photograph of defendant’s face, the page included greetings addressed to him by name and relation, and the page owner’s interests matched that of the defendant.
Various federal cases have addressed the issue of authentication by extrinsic evidence, including U.S. v. Lewisbey[11] and U.S. v. Barnes.[12] In Lewisbey, the Facebook page had defendant’s name, date of birth, residence, and hundreds of pictures of defendant. In Barnes, a witness testified that she had seen the defendant using Facebook and that she recognized his Facebook account as well as his style of communicating as reflected in the disputed message.
In Conclusion
Do your Google searches (or hire a teenager to do it for you), find the nuggets, and convince the judge and jury “it is what it is claimed to be.”
Note: Some of the content in this article came from consultation with highly skilled trial attorneys Christina Moore, Assistant Public Defender in the Alameda County Public Defender’s Office, and Hanni Fakhoury, formerly an Assistant Federal Defender in the Northern District of California and now a Partner at Moeel Lah Fakhoury LLP, specializing in complex criminal defense, civil rights and appellate litigation.
[1]California Rule of Professional Conduct 1.3, “A lawyer shall act with reasonable diligence…in representing a client.” Reasonable diligence means to act “with commitment and dedication to the interests of the client….”
[2]Please be aware that there are ethical considerations when performing these searches, and contacting and communicating with parties, witnesses, or jurors via social media, particularly where a profile is set to private, or if the individual is represented by counsel. This article does not address these issues.
[3]There are digital forensic companies that download entire profiles and put the content into easily searchable databases if there is large amount of information and/or the case merits spending the money.
[4]An image or recording that has been convincingly altered and manipulated to misrepresent someone as doing or saying something that was not actually done or said. (https://www.merriam-webster.com/dictionary/deepfake.)
[5]There are occasions when social media platforms possess information not accessible to the public that may be accessible through subpoena (e.g. IP addresses that provide information used to identify anonymous posters who may be witnesses or parties, or information stored on servers). This is beyond the scope of this article.
[6]Cal. Evid. § 1400; Fed R. Evid. § 901.
[7]Cal. Evid. §356 and Fed R. Evid. § 106.
[8]People v. Beckley (2010) 185 Cal.App.4th 509.
[9]People v. Valdez (2011) 201 Cal.App.1429.
[10]People v. Goldsmith (2014) 59 Cal.4th 258.
[11]U.S. v. Lewisbey, 843 F.3d 653 (7th Cir. 2016)
[12]U.S. v. Barnes, 803 F.3d 209 (5th Cir. 2015)